Web Portal
Understand the role of the ComplyVigilance Web Portal in managing enriched compliance scan results.
ComplyVigilance Web Portal
The ComplyVigilance Web Portal is the central interface for managing and reviewing compliance scan results.
It provides a unified view of all scan activities triggered via the cvclient CLI and desktop app , enabling users to monitor software components, understand their compliance posture, and access detailed insights derived from the AI-powered ComplyVigilance Knowledge Base (CV KB).
The portal plays a key role in organizing projects, storing historical scan data, and surfacing enriched metadata that supports license tracking, vulnerability analysis, and dependency visualization.
How Scan Results Are Generated and Sent to the Portal
To begin scanning, a project must first be created in the Web Portal by an authorized user. Once the CLI executes a scan, it collects relevant package and dependency data and transmits the raw results to the portal using the access token.
The Web Portal receives this data and processes it through the ComplyVigilance Knowledge Base, where it is enriched with:
- License classification details
- Vulnerability mappings with severity and CVE references
- Dependency relationships (direct and transitive)
- Component metadata like version and ecosystem
These enriched results are then made accessible on the Dashboard, where users can explore scan histories, track risk indicators, and align findings with their organization’s compliance requirements.
Scan Result Structure
Each scan result in the ComplyVigilance Web Portal includes the following fields:
| Field | Description |
|---|---|
| Component Name | Name of the software package/component identified during the scan. |
| Version | Exact version of the component detected. |
| Version Expression | Declared version range from the source code or manifest. (e.g., ^3.0, >=2.5). |
| Match Type | Method used to detect the component (e.g., package_manager, container_image). |
| Dependency Type | Indicates whether the component is a direct,transitive or floating dependency. |
| Licenses | Detected software license(s) for the component (e.g., MIT, Apache 2.0). |
| Vulnerabilities | Breakdown of vulnerabilities by severity: Critical (C), High (H), Medium (M), Low (L). |
| Usage Details | Indicates where the component is being referenced or used within the source code. |
| Dependency Graph | Visual link to the graph showing how this component connects to others. |
Component Name
The Component Name identifies the software package or module detected during the scan.
It is typically extracted from package manifests (e.g., package.json, requirements.txt, pom.xml) or container image metadata.
Each component name reflects the naming convention of its respective package manager or ecosystem (e.g., PyPI, npm, Maven).
Version
The Version represents the exact version of the component that was detected during the scan. This version is resolved by the CLI at scan time and helps determine the specific license, vulnerabilities, and metadata associated with that release.
Version Expression
The Version Expression indicates the original version range or constraint defined in the source code or manifest file.
Examples include:
^3.0.0– allows compatible minor updates>=2.5,<3.0– bounded version range
It reflects how the version was specified in the project but may not represent a concrete resolved version.
Match Type
The Match Type describes the method used to detect the component. It can include:
package_manager– found through manifest-based dependency resolutioncontainer_image– found through container inspection
This field helps indicate the source and confidence of detection.
Dependency Type
The Dependency Type classifies how the component is included in the project:
direct– explicitly declared in the project’s dependenciestransitive– pulled in indirectly by another dependencyfloating– ependency that exists in the project without an explicitly defined relationship to the declared dependency hierarchy.
Understanding this helps prioritize risks and visibility.
Licenses
The Licenses field lists the detected software licenses associated with each component. These are identified through license files, metadata, or package headers. ComplyVigilance categorizes licenses into standardized types to support legal review and risk assessment:
- Public Domain
- Patent License
- Proprietary Free
- Copyleft Limited
- Free Restricted
- CLA (Contributor License Agreement)
- Copyleft
- Commercial
- Unstated License
- Permissive
- Source-available
- Uncategorized
These categories help organizations determine license compatibility, redistribution rights, and potential legal obligations.
Multiple licenses may appear for multi-licensed components, and the Uncategorized category indicates that a license was detected but could not be mapped to any classified license category.
Vulnerabilities
The Vulnerabilities field shows known security issues tied to the component.
Each vulnerability is classified by severity:
- C – Critical
- H – High
- M – Medium
- L – Low
These severities are determined based on CVE databases and scoring systems (e.g., CVSS). Clicking on them usually opens detailed vulnerability reports.
Usage Details
Usage Details indicate where and how the component is being used within the source code, if detected.
This includes the file path where the component is used, along with the exact import statement detected in the source code. If no usage data is available, this field may show No Details.
Dependency Graph
The Dependency Graph provides a visual representation of the component’s relationship to other packages in the project.
It helps identify:
- Parent-child relationships between components
- Chains of transitive dependencies
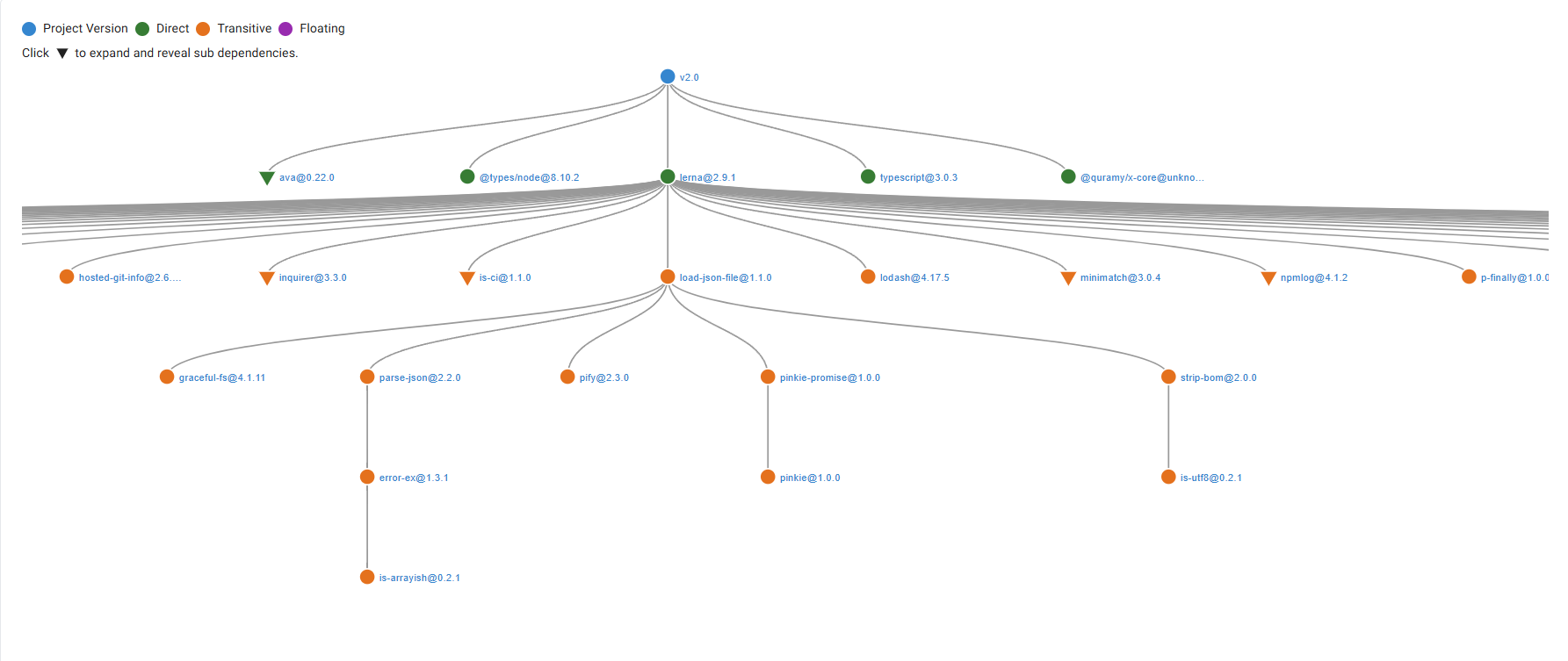
Users can explore these graphs to better understand package origin and propagation.